I had been playing with Nambu until I was working in blender tonight and had the OSX console up and running.. What did I see it logs the user and password in the clear in the system.log file… BAD BAD BAD!!!!! Their response, “it is beta software so it does extensive logging…” Well you don’t need to log the freaking password and username in the CLEAR. Needless to say no more nambu till they fix that..
Ultra Restricted Shell in Solaris
How to setup a readonly environment on Solaris:
If you want to give a specific user readonly access to your solaris machine via ssh, and want to log everything they do, it is sort of easy to setup. Here is a quick step-by-step guide to setting it up.
1. First you will need to chose what restricted shell you want to use. In this case I used bash as I wanted the .bash_history file to contain the exact time every command was run on the system. Since Solaris does not come with the rbash command, the only thing you need to do is make a copy of /usr/bin/bash to /usr/bin/rbash.
2. Make the user’s shell be /usr/bin/rbash, this will make them use the restricted bash shell.
3. Make their home directory owned by root.
4. Make their .profile owned by root
5. Create a .bash_history file and make it owned by that user. This should be the only file in their directory that is owned by the user.
6. Pick a location for your “restricted” binaries to reside. If this user will be logging in to multiple machines and you have a shared file system (say /home) I would suggest making the directory in /home; say /home/rbin.. This way you only have to put /home/rbin in their PATH.
7. Make symbolic links in your restricted binary directory to the binaries you want to run. I.e. ls, ps, more, prstat,passwd and hostname :
lrwxrwxrwx 1 root root 17 Feb 19 20:47 hostname -> /usr/bin/hostname*
lrwxrwxrwx 1 root root 11 Feb 19 19:56 ls -> /usr/bin/ls*
lrwxrwxrwx 1 root root 13 Feb 19 19:57 more -> /usr/bin/more*
lrwxrwxrwx 1 root root 15 Feb 19 19:56 prstat -> /usr/bin/prstat*
lrwxrwxrwx 1 root root 11 Feb 19 19:56 ps -> /usr/bin/ps*
lrwxrwxrwx 1 root root 11 Feb 19 19:56 passwd -> /usr/bin/passwd*
By making these sym links instead of the actual binaries, you do not have to worry if you have multiple platforms that you are going between (i.e. Sparc, x86) and doing custom logic to use the right binary.
8. Create the users .profile with the following in it:
readonly PATH=/home/rbin
readonly TMOUT=900
readonly EXTENDED_HISTORY=ON
readonly HOSTNAME="`hostname`"
readonly export HISTTIMEFORMAT="%F %T "
readonly export PS1='${HOSTNAME}:${PWD}> '
This will make it so they can not change any of the Environment variables. It sets their path to /home/rbin. Sets a inactivity time out to be 15 minutes. Sets the extended history to be on (this logs the time each command was executed in their .bash_history file). And finally sets their prompt and makes it readonly as well.
9. The last thing you need to do is change the permissions on the scp and sftp-server binaries so that the user can not execute them. Otherwise, they would be able to download files and go any where on the server they want. (Restricted shell will prevent them from cd’ing out of their home directory) To do this, I created a group and put my user in it as their primary group. Say the group was called rdonly. Now I do the following:
setfacl -m group:rdonly:--- /usr/lib/ssh/sftp-server
setfacl -m group:rdonly:--- /usr/bin/scp
So the files should show up like this now:
bash-3.00# ls -la /usr/lib/ssh/sftp-server /usr/bin/scp
-r-xr-xr-x+ 1 root bin 40484 Jan 22 2005 /usr/bin/scp
-r-xr-xr-x+ 1 root bin 35376 Jan 22 2005 /usr/lib/ssh/sftp-server
And the getfacl will look like this:
bash-3.00# getfacl /usr/bin/scp
# file: /usr/bin/scp
# owner: root
# group: bin
user::r-x
group::r-x #effective:r-x
group:rdonly:--- #effective:---
mask:r-x
other:r-x
This makes it so when the user tries to sftp or scp in to the machine, it will immediately disconnect them as they don’t have permissions to run those 2 executables.
That is about it. Don’t forget to set their password, make sure it has a policy set on it to be changed often and require a combination of letters, numbers and special characters and that it is at least 8 characters in length.
So now when the user logs in they will see something similar to this:
[laptop:~] unixwiz% ssh unixwiz@fozzy
Password:
Last login: Thu Feb 19 22:10:15 2009 from laptop
fozzy:/home/unixwiz> cd /
-rbash: cd: restricted
fozzy:/home/unixwiz> vi /tmp/test
-rbash: vi: command not found
fozzy:/home/unixwiz> PATH=$PATH:/usr/bin
-rbash: PATH: readonly variable
fozzy:/home/unixwiz> timed out waiting for input: auto-logout
As you can see, it will give you errors if you try to do something that you are not allowed to do. The last line shows the time out message where it closes the connection due to inactivity.
Now if the administrator goes and looks at the users .bash_history file they would see this:
#1235099570
cd /
#1235099577
vi /tmp/test
#1235099587
PATH=$PATH:/usr/bin
The #number is the exact time that the user ran the command below it. The item is the seconds since the epoch…
AIX Most secure OS? Think not.
IBM’s Xforce published their new 2008 annual report. In it they had this chart:
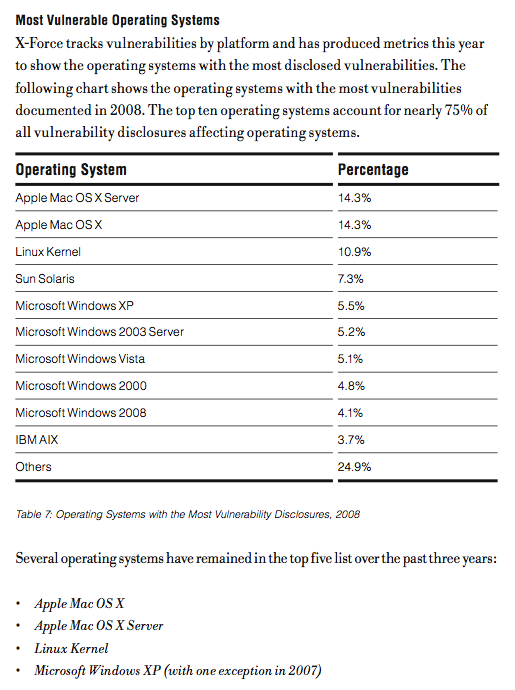
Surprising is that IBM put’s one of their own OS’s near the bottom of the list. Some of my opinions are :
1. No one uses AIX that much, so no one looks for holes in the code.
2. Any one who uses AIX, doesn’t have it directly connected to the Internet.
3. It is so cost prohibitive to use, that people are looking at Solaris/Linux or Windows to run their business on.
But the funniest thing about this is the last I used AIX the following were still done on install by IBM:
1. telnet enabled
2. root logins allowed remotely
3. no ssh comes with the OS, you have to install a crappy “linux toolkit”, and then install another 10 different packages to get SSH enabled.
4. No RBAC
5. Syslog configuration does not exist
6. Root does not even have a password on install
Seems to me that IBM needs to fix some fundamental issues with their OWN OS before they can say it is not one of the “Most Vulnerable Operating Systems”.
The funniest issue with this is for MacOSX to be listed at the top, all most all of those require some one to actually run something on the machine with administrative privileges.
Increase in Solaris patch cluster size
Justin pointed out to me tonight that the new Recommended and Security patch clusters for Solaris 10 were quite large. And right he was.. It seems that in the last month or so the 10 Recommended patch cluster has grown from 400meg to over 1GB in size now. (not to mention that he said you need almost 2.5 gig of space to unzip it.)
Looking at the cluster readme, I can take a guess as to why it is so large, there are multiple kernel patches. There are also updates to Firefox, Thunderbird, Adobe Acrobat Reader, Adobe Flash plugin, multiple Java Updates and a patch for the defunct Mozilla 1.7 browser (which in my opinion should just be removed completely).
The interesting part is that the X86 patch cluster is over 300Meg smaller than the sparc one. The only major difference that I can think of is that X86 doesn’t have Adobe Acrobat Reader yet.
I wish Sun would just offer a ISO download of all the patches now (sort of like the EIS dvd) for the public. Also need to find a faster way to download the patches.
Checkfree hacked?
As I was going through mail tonight, gmail had marked this message as spam, but it appears as though something actually happened and checkfree lost control of its domain for a while…..
We take great care to keep your personal information secure. As part of these ongoing efforts, we are notifying you that the computer you use for online bill payment may have been exposed to software that puts the security of your computer’s contents at risk. This letter will help you determine if your computer is actually infected and advise you how to fix the problem and protect yourself against future risk.
The malicious software affects some but not all customers who accessed online bill payment on Tuesday, December 2, 2008. For a limited period of time, some customers were redirected from the authentic bill payment service to another site that may have installed malicious software. Your computer may be infected if all of the following are true:
- You attempted to access online bill payment between 12:30 a.m. and 10:10 a.m. Eastern time (GMT -5) on Tuesday, December 2, 2008, and
- You were using a computer with the Windows operating system, and
- You reached a blank screen rather than the usual bill payment screen when you attempted to navigate to online bill payment, and
- After reaching the blank screen, your computer’s virus protection program did not tell you via pop-up or other messaging that malicious software was detected and quarantined.
If all four of the conditions above are true, your computer may be infected. We have partnered with McAfee, the world’s largest dedicated security technology company, to provide you with a complimentary copy of its VirusScan Plus software which, when installed, will detect, block and remove any malicious software from your computer hard drive. Please contact us at 877-800-4864 for further instructions or 800-564-9184 (Option 1) for further instructions. We will also offer you both advice and free services that can help you mitigate any risk you may face as a result of this incident or other everyday exposures you may encounter.
CheckFree will never ask for your password via email or via phone. If you ever receive an email requesting your password, do not respond and delete the email immediately.
We value your business and your trust, and we apologize for any inconvenience this incident has caused.
Thank you,
Art D’Angelo
Vice President, CheckFree Customer Operations
More links that I found:
Online Payment Site Hijacked By Notorious Crime Gang
